Harshani Somarathne
Tuesday, September 25, 2018
Wednesday, May 23, 2018
How to implement a web application that provides a RESTful API
From this blog post lets get to know how to implement a resource server API
First lets get to know what and how this normally work. The below diagram will be able to give you a good idea .
If you want you can use existing authorization server like wso2 identity server. But I created authorization server and resource server both in a single api. There is an endpoint that you can call in order to retrieve the resources.
This is written using node.js. In order to run this on your computer you have to have node.js installed on your computer.
The sample code is uploaded to the Github and the link is mentioned below.
Run the application as follows
First lets get to know what and how this normally work. The below diagram will be able to give you a good idea .
If you want you can use existing authorization server like wso2 identity server. But I created authorization server and resource server both in a single api. There is an endpoint that you can call in order to retrieve the resources.
This is written using node.js. In order to run this on your computer you have to have node.js installed on your computer.
The sample code is uploaded to the Github and the link is mentioned below.
Run the application as follows
- Install and run nodejs application after you download the project,use terminal to go application folder
- Type npm install package.json
- Run the app using nodejs server.js or using nodemcu server.js
- Open web browser and goto http://localhost:3000
Monday, May 21, 2018
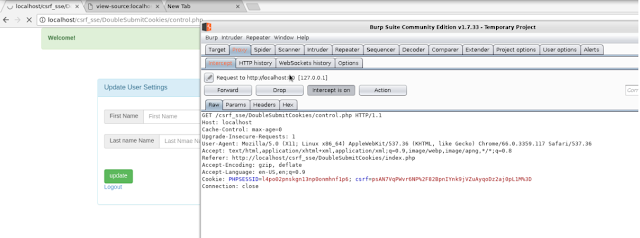
Double Submit Cookies Patterns
Before we begin to learn what a Double submit cookie pattern is , lets learn what a double submit cookies is. A definition that we could use is that is sending a random value in both a cookie and as a request parameter, with the server verifying if the cookie value and request value match.
When a user authenticates to a site, the site should generate a (cryptographically strong) pseudorandom value and set it as a cookie on the user's machine separate from the session id. The site does not have to save this value in any way, thus avoiding server side state. The site then requires that every transaction request include this random value as a hidden form value (or other request parameter). A cross origin attacker cannot read any data sent from the server or modify cookie values, per the same-origin policy. This means that while an attacker can force a victim to send any value he wants with a malicious CSRF request, the attacker will be unable to modify or read the value stored in the cookie. Since the cookie value and the request parameter or form value must be the same, the attacker will be unable to successfully force the submission of a request with the random CSRF value.
Following can be used if you require to have additional defenses to strengthen double submit cooki patters
- HTTP Strict Transport Security (HSTS)
- Cookie Prefixes ("__HOST-" the one you want)
- Sign cookie to user
- Use custom HTTP header to send request token
This is how we can do double submit cookie
using java-script we can load csrf token into form filed with hidden values. also in here we also check user submissions in back end,whenever user request a page he/she gets a totally random value, so he/she cant predict it and perform exploitation againts legitimate users
And remember to set cookie domain,this prevent from reading cookie value from another address rather than you mentioned one
Monday, May 7, 2018
Cross-site Request Forgery protection in web applications via Synchronizer Token Patterns
Cross-site request forgery, also known as one-click attack or session riding and abbreviated as CSRF . This is a type of malicious exploit of a website where unauthorized commands are transmitted from a user that the web application trusts. There are many ways in which a malicious website can transmit such commands; specially-crafted image tags, hidden forms, and JavaScript XMLHttpRequests, for example, can all work without the user's interaction or even knowledge. Unlike cross-site scripting (XSS), which exploits the trust a user has for a particular site, CSRF exploits the trust that a site has in a user's browser.
Following is how a page that has Synchronizer Token Patterns work
Following is how a page that has Synchronizer Token Patterns work
To prevent CSRF attacks we can use simple method such as generating a random string in server side and append it to body of front end and check the both values when user submit web page. also we can use methods such as Check standard headers to verify the request is same origin.
Synchronizer (CSRF) Tokens
- Any state changing operation requires a secure random token (e.g., CSRF token) to prevent CSRF attacks
- Characteristics of a CSRF Token
- Unique per user session
- Large random value
- Generated by a cryptographically secure random number generator
- Add token to session and check it in backend
- The CSRF token is added as a hidden field for forms or within the URL if the state changing operation occurs via a GET
- The server rejects the requested action if the CSRF token fails validation
in these example code i’ve used an openssl function to generate a secure random string,you can find it in source code.
this can be monitored when a user sends a messageMonday, October 23, 2017
Learn to hide your Files
I'm going to introduce a software called "mylockbox" which allows you to hide and protect your data from unauthorized access.
First of all you have to download the software using below link.
https://my-lockbox.en.softonic.com/
Once you dowload the software you can see a zip file and extract it.
This is a normal installation like other mini software.
Installation Process
After that click on Finish !!!!
Then open the software,you can see a dialog box like this.
Enter password -> give a strong password more than 8 characters including upper & lower case, special characters, symbols and numbers. Ex: *gsWjk56@3
Confirm Password-> Re-enter the password that you have been entered.
Hint-> Enter some hint if you really want to remember the password.
Then you have to choose a file, folder or partition which you wish to hide your data.
Then if you want to unlock your data,Simply double click on the software and enter the password.Then you can see your data as it is.
Friday, October 20, 2017
Are we safe in WhatsApp ?
I'm sure that almost all of us have used WhatsApp but the big question is are we secure enough?
Well that's why i'm writing this blog post to let you know the security issues that you should pay attention to.
Imagine what if If WhatsApp were forced to create a backdoor into its service that allowed governments to spy on suspected terrorists, it would compromise the security of millions of users data.Another fact we have to pay attention is that WhatsApp claims this loophole exists so that if someone changes their phone, and therefore their automatic security key, messages will still send so as not to disrupt service.
Unencrypted Backups
There is an end to end encryption system , that means that only your device has the ability to decode them. This stops your messages being intercepted during transmission , but it doesn't mention of their safety while on the device. On both iOS and Android it is possible to create a backup of your messages to either iCloud or Google Drive. The backups that WhatsApp create contain the decrypted messages on your device.
Encryption Vulnerabilities
Keys are used to verify the messages transmitted . This key can be changed when reinstalling the app or moving to a new phone.
How ever WhatsApp had the ability to change security keys for offline users, they may be able to intercept and decrypt messages. WhatsApp could then force you to resend your messages with the new security key, and allow themselves access to the messages.
Now lets find out some answers for some common questions people have about the security in WhatsApp
Do we have to turn on encryption ?
As a user, you don’t have to turn this feature on, nor can you turn it off. You should receive a message within your chats if you are using the latest version of the app (which is required) to let you know the change has been implemented for you.
Whats the End to end encryption meaning ?
When you send a message, it can only be ‘unlocked’ by the intended recipient.
Thursday, October 19, 2017
Linux Basics - Directory and File Commands
Before
moving to commands related to files and directory manipulation commands, it is
important to understand the structure of the file system in Linux.
Unlike
in Windows file system where you can find separate partitions like C:/,
Linux has a root directory denoted by /. root directory is the
beginning of the Linux file system.
Root
directory contains sub directories and files.
No 01 :- ls
The ls command - the list command - functions in the Linux terminal to show all of the major
directories filed under a given file system. For example, the command:
No 02 :- cd
The
cd command - change directory - will allow the user to change between file
directories. As the name command name suggest, you would use the cd command to
circulate between two different directories.
No 03:- mv
The
mv command - move - allows a user to move a file to another folder or
directory. Just like dragging a file located on a PC desktop to a folder stored
within the "Documents" folder, the mv command functions in the same
manner.
No 04:- man
The
man command - the manual command - is used to show the manual of the inputted
command. Just like a film on the nature of film, the man command is the meta
command of the Linux CLI.
No 05 :- mkdir
The
mkdir - make directory - command allows the user to make a new directory. Just
like making a new directory within a PC or Mac desktop environment, the mkdir command
makes new directories in a Linux environment.
No 06:- rmdir
The
rmdir - remove directory - command allows the user to remove an existing
command using the Linux CLI.
Database Security
Databases often hold the major importance of an organization; Its’ transactions, customers, employee info, financial data for both the company and its customers, and much more are all included in databases, mostly controlled by the hands of a database administrator with no security training.
Database security and integrity are essential aspects of an organization’s security posture.
What Is Database Security?
Database security, protects the confidentiality, integrity and availability of an organization’s databases.Database security should consist of the following
- Software – software is used to ensure that people can’t gain access to the database through viruses, hacking, or any similar process.
- Physical controls – an example of a physical component of database security could be the constant monitoring of the database by company personnel to allow them to identify any potential weaknesses and/or compromises.
- Administrative controls – this refers to things like the use of passwords, restricting the access of certain people to certain parts of the database, or blocking the access of some company personnel altogether.
functions of database security include
- Blocking attacks from unauthorized users or hackers.
- Preventing malware infections and stopping viruses stealing data.
- Ensuring that physical damage to the server doesn’t result in the loss of data.
- Prevents data loss through corruption of files or programming errors.
Database Security Best Practices:
- Protect against SQL injections by using parameterized queries to keep malicious queries out of your database.
- Ensure your database administrators both understand the business value and importance of ensuring your databases are secured and extending them the resources to do so properly.
- Static Code Analysis is an essential tool for organizations developing applications as portals to databases to slash SQL injection, buffer overflow, and mis-configuration issues.
- Maintain CIA by keeping your databases up to date, removing any unknown components, and enforcing least privilege parameters to ensure the confidentiality, integrity and availability of your databases.
- To maintain availability, employ an Uninterruptible Power Supply, or UPS, to ensure any forced shutdown doesn’t cause data loss.
How to make you mobile theft proof
Following are few steps that you can
follow to secure your mobile devices form attackers. Security countermeasures are being developed and applied to
Smartphone, from security in different layers of software to the dissemination
of information to end users. There are good practices to be observed at all
levels, from design to use, through the development of operating
systems , software layers, and downloadable apps.
How to
1.
Add protection
You can
activate the security features in the phone. Apple
device users can enable the “Find My iPhone” or “Find My iPad” feature in
iCloud, which will help them locate the device if it is missing and erase the
data on it. New Apple devices also include an activation lock feature that
prevents the devices from being reactivated without the owner’s credentials.
Android device users can log into Android Device Manager to locate their
devices on a map and set up the lock and erase capabilities.
2.
Set a strong password
choose long, complex passwords
for their devices, instead of using the standard four-digit code. A strong
password is at least eight characters long and includes a combination of
letters, numbers and special characters. Employees should also set their
screens to lock after a period of inactivity — for example, two minutes.A
strong password can provide a valuable layer of protection for mobile data.
What to do if your device is lost or stolen
1. Report the missing device
Contact the specialist
organization to stop the record to anticipate unapproved utilization. The
transporter may likewise add the gadget to a worldwide database of boycotted
telephones, which can help prevent another client from initiating it.
Additionally tell the police and give them the gadget's area and whatever other
data that could recover it.
2. Wipe the Device
If you believe sensitive
data stored on the device may be at risk, wipe it remotely. This will reset the
device to its factory installed settings. Any passwords stored on the phone
should be changed as an extra precaution. For example, if an email password is
automatically saved in an email application or a banking password is kept in a
note-taking app on the device, the owner should log into the email or banking
service from another device and reset it.
Contact the service
provider to put a hold on the account to prevent unauthorized usage. The
carrier may also add the device to a global database of blacklisted phones,
which can help stop another user from activating it. Also notify the police and
give them the device’s location and any other information that could help to
retrieve it.
What
are the consequences of mobiles not being secured?
·
The attacker can change your phone
to a zombie machine
·
A compromised Smartphone can
record conversations between the user and others and send them to a third party
·
The attacker can prevent the
operation and/or be starting of the Smartphone by making it unusable
·
The attacker can remove the
personal (photos, music, videos, etc.) or professional data
Cyber espionage

Cyber espionage is a threat that’s being heard
more and more all the time and there have been a flood of stories in 2009 on
this subject. Most of these incidents surround government bodies and agencies
and therefore have not been a huge threat to most individual organizations.
However, since cyber espionage has major implications for the government, it is
a rising threat that must be closely monitored.
Who performs these acts ?
Normally these are done by attack groups.
Other than attack groups
·
state actors whom are acting on behalf
of a governmental body
·
patriotic hackers
·
Hacktivists
·
Scammers
·
Data thieve
All of the above can be involved in cyber
espionage.
Some attackers are out to steal intellectual
property in order to damage businesses, others are going after sensitive government.
What are the
objectives of cyber espionage?
·
Steal valuable trade secrets
·
Surveillance virus
·
Intellectual property
·
Confidential business strategies.
·
To eavesdrop on financial transactions
·
Disable industrial control systems.
·
Political reasons( nuclear, weapons)
·
Intimidation
Now let’s get to know the reasons behind these
attacks.
What are the
reasons of cyber espionage?
·
To gain knowledge or information of nations
military operations
·
To identify the strength of other nations and
to zero in on infrastructure
·
To have a competitive advantage against
adversaries
·
To build defense and weaken other states
·
To generate revenue
·
To destroy critical infrastructure of victims
·
To gather intelligence of operations
Counter measures for cyber espionage
·
Patch management
·
Configuration management
·
Antivirus
·
Encryption
·
Firewalls
·
Intrusion Detection and Intrusion Prevention
System
·
Biometric locks
·
Access control lists
·
Vulnerability and Risk Assessments
·
Authentication and Authorization
How Passwords are stolen!
Ever
wondered how your passwords could get to the hands of hacker ? well lets get to
know how.
I
have listed few ways on how your passwords could get to the hands of hacker and
a guide on how to create a proper password.
·
Dictionary
attacks
Dictionary
attacks are done using programs that cycle through a predetermined list of
common words often used in passwords. Passwords with words or phrases are weak
and that the easiest for these programs to predict. To protect your accounts
from dictionary attacks do not use common words and phrases in your passwords.
How to protect your
user passwords from dictionary attacks
- Change
your passwords regularly.
- Do
not use common words or phrases in your password.
- Do
not write down your passwords, or share them with others.
- Use
two-factor authentication (link is external)as
an extra layer of protection .
- Do
not use again the same password across different websites.
·
Password crackers
A
password cracker is a program used to crack passwords by brute force, trying
again and again millions of combinations of characters, until your password is
detected. Shorter and less complex passwords are quicker to guess for the
program. Longer and complex passwords take much longer to guess. If this is the
case, the attacker is more likely to use a dictionary attack because of the
lengthy amount of time it will take for the program to figure out the password.
To protect your user passwords from password crackers use complex passwords.
How to create a
complex password
- Never
use commonly used passwords like “123456,” “password,” “qwerty,” or a word
like “apple.”
- You
must never use phone numbers, addresses, birthdays, your SSN or your name,
the name of a family member or pet in your password.
- Always
try to use a combination of lowercase and uppercase letters, numbers and
symbols in your passwords.
- Create
passwords at least eight characters
long as passwords with more characters and symbols are more difficult to
guess.
- Do
not use words or phrases.
What you must do
if you suspect that your password have been compromised?
First things first , do not delay you must act
fast.
- Try
to figure out the kind of attack.
Was it an online breach or a POS breach?
- Use
two-factor authentication whenever it is able to use.
- Monitor
potentially compromised accounts, especially your online banking accounts.
- Alter
your passwords to complex passwords on all of your accounts, especially if
you tend to reuse the same passwords for different websites.
Subscribe to:
Comments (Atom)
Test Images
Below images are being used for the Hashtag Generator and Content Authenticator research .

-
Have you ever received emails saying that you have won a grand prize or an email claiming it’s something useful, such as a coupon to ...
-
IPsec protocol is a standard that is used in VPNs to secure the IP networks.IPsec protocol also protects and authenticates the IP packets t...